IoT Security Solutions to protect connected devices, networks, and data from cyber threats. We provide secure IoT architecture, encryption, threat detection, and compliance to ensure safe, reliable, and scalable IoT deployments.
iot security solutions
[ AUDIENCE ]
IoT Security Solutions | Protect Connected Devices & Data
Our IoT security solutions help startups, enterprises, and organizations protect connected devices, secure data transmissions, and ensure compliance. We deliver robust, scalable protection tailored to your IoT ecosystem.
[ 01 ]
Smart Tech Stack Advisory
We help you choose the most secure and efficient IoT architecture and technology stack — from edge computing and serverless to hybrid and cloud-native approaches — aligned with your business goals and compliance requirements.
[ 02 ]
Optimized Performance & Scalability
Our experts ensure your IoT systems operate with high performance, low latency, and the ability to scale seamlessly as your connected device network expands.
[ 03 ]
Security-First Strategy
We integrate advanced IoT security protocols, encryption standards, and compliance measures to safeguard devices, data, and communications from cyber threats.
[ 04 ]
Business-Centric Approach
We align IoT security solutions with your business objectives to protect assets, minimize risks, and maximize ROI while supporting sustainable growth.
[ 05 ]
Comprehensive Risk Assessment
We perform thorough IoT security audits to detect vulnerabilities, ensure regulatory compliance, and future-proof your connected infrastructure.
[ BENEFITS ]
Benefits of Our Iot Security Solutions Services
We offer efficient communication channels and flexible scheduling to fit your workflow. Our team delivers regular updates and clear insights, keeping you informed at every stage of the IoT security solutions process.
Highly Qualified IoT Security Experts
We deliver robust IoT security solutions built by experienced engineers and certified cybersecurity specialists. Our expertise ensures the protection of your connected devices, networks, and sensitive data from emerging threats.
Clear Communication & Transparency
We maintain open and clear communication throughout the IoT security implementation process, providing regular updates, detailed reports, and actionable recommendations at every stage.
Tailored Security Solutions
Every IoT ecosystem is unique. We design custom security strategies — from device authentication to encrypted communications — to match your specific infrastructure and compliance needs.
Flexible Engagement Models
We offer adaptable cooperation models and payment options, ensuring our IoT security services align with your budget, project size, and long-term objectives.
Ongoing Protection & Support
Cybersecurity is an ongoing process. We provide continuous monitoring, threat detection, and maintenance to keep your IoT infrastructure safe and future-proof.
[ STEPS ]
Iot Security Solutions Services
Delivering robust and secure IoT security solutions that protect connected devices, networks, and data from cyber threats, ensuring reliability, compliance, and trust across all IoT ecosystems.
[ TECHNOLOGIES ]
The Brain, Heart, and Engine of Every Project We Build
[ TESTIMONIALS ]
Our clients talk about testing the results that we can achieve together.
[ CASES ]
& meet PM consulting cases in our basket
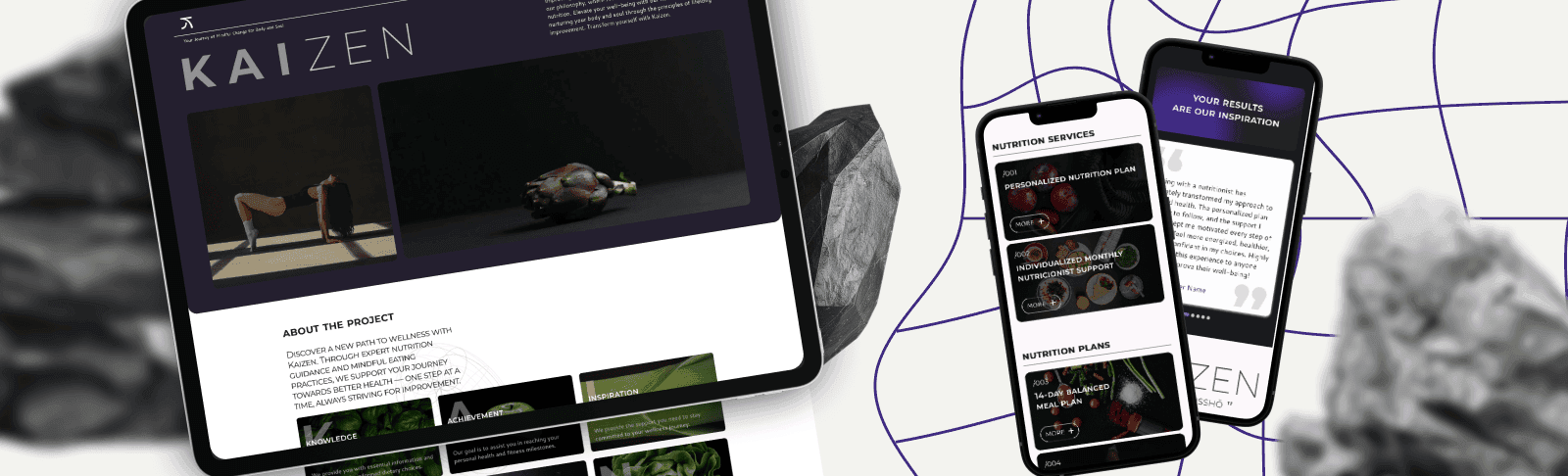
Kaizen
- Journey of Mindful Improvement for Body and Soul
TECHNOLOGIES:
Industry:
Wellness & Nutrition
CLIENT since:
2024
REGION:
ВБ, Лондон
Kaizen 2
- Journey of Mindful Improvement for Body and Soul
TECHNOLOGIES:
Industry:
Wellness & Nutrition
CLIENT since:
2021
REGION:
UK, London
Kaizen 3
- Journey of Mindful Improvement for Body and Soul
TECHNOLOGIES:
Industry:
Wellness & Nutrition
CLIENT since:
2021
REGION:
UK, London
[ FAQS ]
[ 1 ]
What are the biggest threats to IoT systems?
Common threats include unauthorized access, data breaches, malware attacks, device hijacking, and insecure network communications.
[ 2 ]
How do you secure IoT devices?
By implementing encryption, strong authentication, firmware integrity checks, secure APIs, and continuous monitoring for suspicious activities.
[ INSIGHTS ]
explore Expert Insights
October, 3, 2025
Web Development![[object Object]](https://pub-5636fbedb0bb4d84bd7be9abf807b53e.r2.dev/seo_improvement_119f43d7a4.png)
How to speed up landing, funnel and eCommerce pages without extra complexity
What problems do you encounter? Pages open slowly, the first screen is blank for a few seconds, images are “heavy,” forms and widgets freeze (especially on mobile devices). As a result, people don't see the offer in time, the bounce rate increases, there are few applications, and advertising eats up the budget; pages also perform worse in search results. What this article will give you. In simple terms, we will analyze how to show the content immediately, reduce the “weight” of the page, prioritize the main action, and get a noticeable increase in conversion. You will see quick steps for 7 days, a minimum plan for switching to Astro, and answers to typical objections from landing page owners.
February, 14, 2025
![[object Object]](https://pub-5636fbedb0bb4d84bd7be9abf807b53e.r2.dev/Devops1_3ddffbec49.jpeg)
Discover the latest advancements in software development, from AI-driven automation to cloud computing innovations. Stay ahead of the curve with insights into the technologies that are transforming businesses today.
February, 14, 2025
![[object Object]](https://pub-5636fbedb0bb4d84bd7be9abf807b53e.r2.dev/Ep_Oqf_O6d_400x400_8664425073.png)
Test blog
Discover the latest advancements in software development, from AI-driven automation to cloud computing innovations. Stay ahead of the curve with insights into the technologies that are transforming businesses today.


Yulia Dantes
Founder, CEO
UniCode Software built a great site, captured my vision, and delivered on time.
I want to say thank the amazing Unicode Software team who created my website, https://kaizenproject.net. From the very beginning, they listened carefully to my vision and brought it to life with great attention to detail. The design is clean, professional, and truly reflects the values of Kaizen Project. Communication was smooth, deadlines were met, and the final result exceeded my expectations. I’m incredibly grateful for their hard work and would gladly recommend them to anyone looking for a reliable and talented web development team.
Yulia Dantes
Founder, CEO
UniCode Software built a great site, captured my vision, and delivered on time.
I want to say thank the amazing Unicode Software team who created my website, https://kaizenproject.net. From the very beginning, they listened carefully to my vision and brought it to life with great attention to detail. The design is clean, professional, and truly reflects the values of Kaizen Project. Communication was smooth, deadlines were met, and the final result exceeded my expectations. I’m incredibly grateful for their hard work and would gladly recommend them to anyone looking for a reliable and talented web development team.
Yulia Dantes
Founder, CEO
UniCode Software built a great site, captured my vision, and delivered on time.
I want to say thank the amazing Unicode Software team who created my website, https://kaizenproject.net. From the very beginning, they listened carefully to my vision and brought it to life with great attention to detail. The design is clean, professional, and truly reflects the values of Kaizen Project. Communication was smooth, deadlines were met, and the final result exceeded my expectations. I’m incredibly grateful for their hard work and would gladly recommend them to anyone looking for a reliable and talented web development team.
Yulia Dantes
Founder, CEO
UniCode Software built a great site, captured my vision, and delivered on time.
I want to say thank the amazing Unicode Software team who created my website, https://kaizenproject.net. From the very beginning, they listened carefully to my vision and brought it to life with great attention to detail. The design is clean, professional, and truly reflects the values of Kaizen Project. Communication was smooth, deadlines were met, and the final result exceeded my expectations. I’m incredibly grateful for their hard work and would gladly recommend them to anyone looking for a reliable and talented web development team.
Yulia Dantes
Founder, CEO
UniCode Software built a great site, captured my vision, and delivered on time.
I want to say thank the amazing Unicode Software team who created my website, https://kaizenproject.net. From the very beginning, they listened carefully to my vision and brought it to life with great attention to detail. The design is clean, professional, and truly reflects the values of Kaizen Project. Communication was smooth, deadlines were met, and the final result exceeded my expectations. I’m incredibly grateful for their hard work and would gladly recommend them to anyone looking for a reliable and talented web development team.